Deepfakes are everywhere.
Voice clones. Video fakes. Impersonation scams.
Every day, families lose millions to scammers using AI to clone voices and faces. Companies wire money to fake executives. Parents panic over kidnapping hoaxes.
How do you know who's real anymore?
Verify using memories, not passwords.
realxreal turns your shared experiences into unbreakable authentication.
Memory-Based Challenges
Verify identity through shared experiences only real people know. No AI can fake your memories.
Pre-Call Verification
Authenticate before the conversation starts. Know who you're talking to before you pick up.
Zero-Retention
Your private keys never leave your device. Memory challenges are processed in real-time and immediately discarded—never stored.
Your Data, Not Ours
We don't sell your info or mine your data. Your contact list and personal memories stay on your phone, where they belong.
Device-Bound Security
Cryptographic keys stored in Secure Enclave. Each device is uniquely authenticated.
Open Source Protocol
The Doppelgänger Protocol™ is publicly auditable. Security through transparency.
See It In Action
Simple, secure, and built for everyone
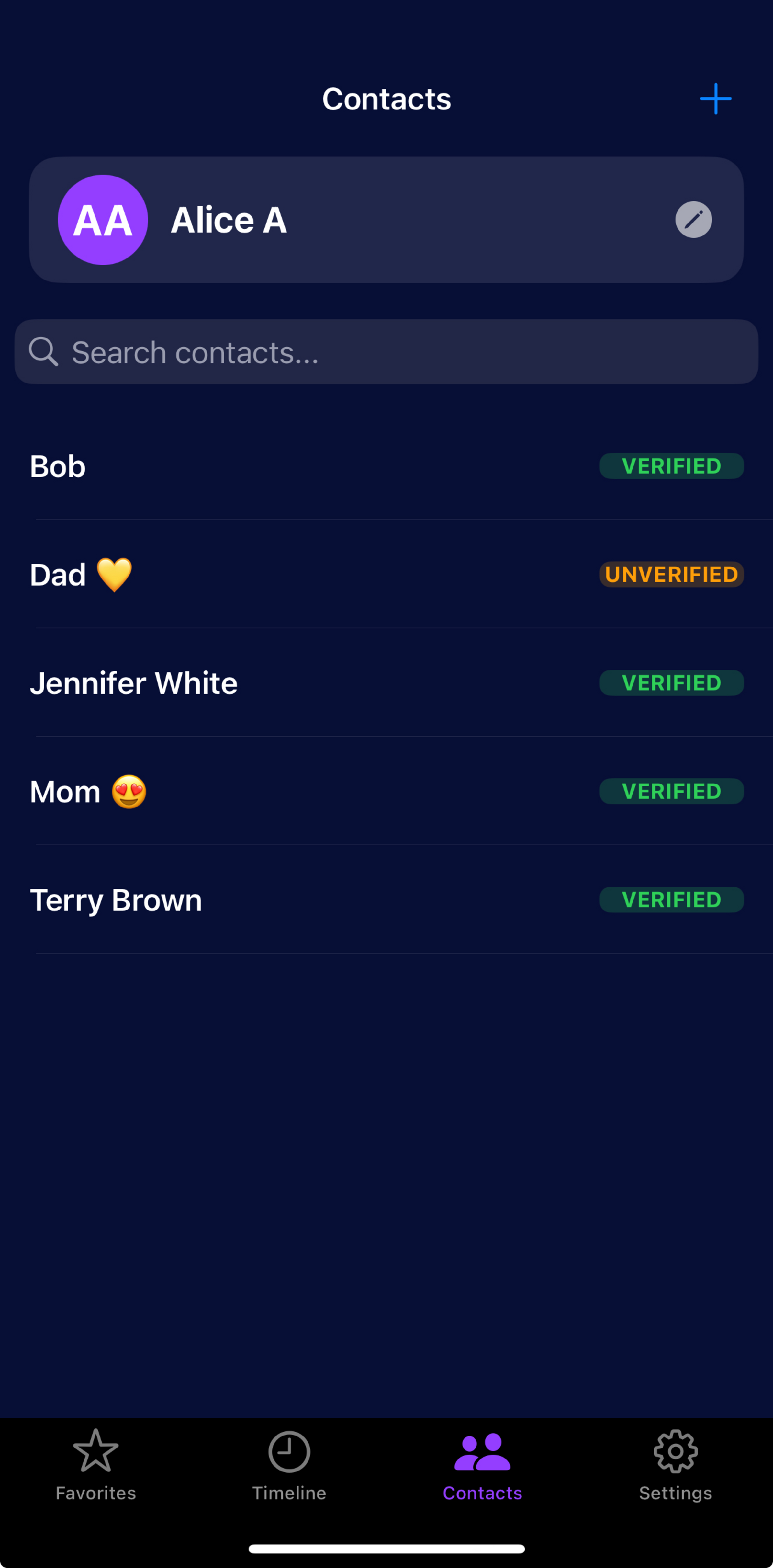
Your Trusted Network
Manage your verified contacts. See who's authenticated and when.
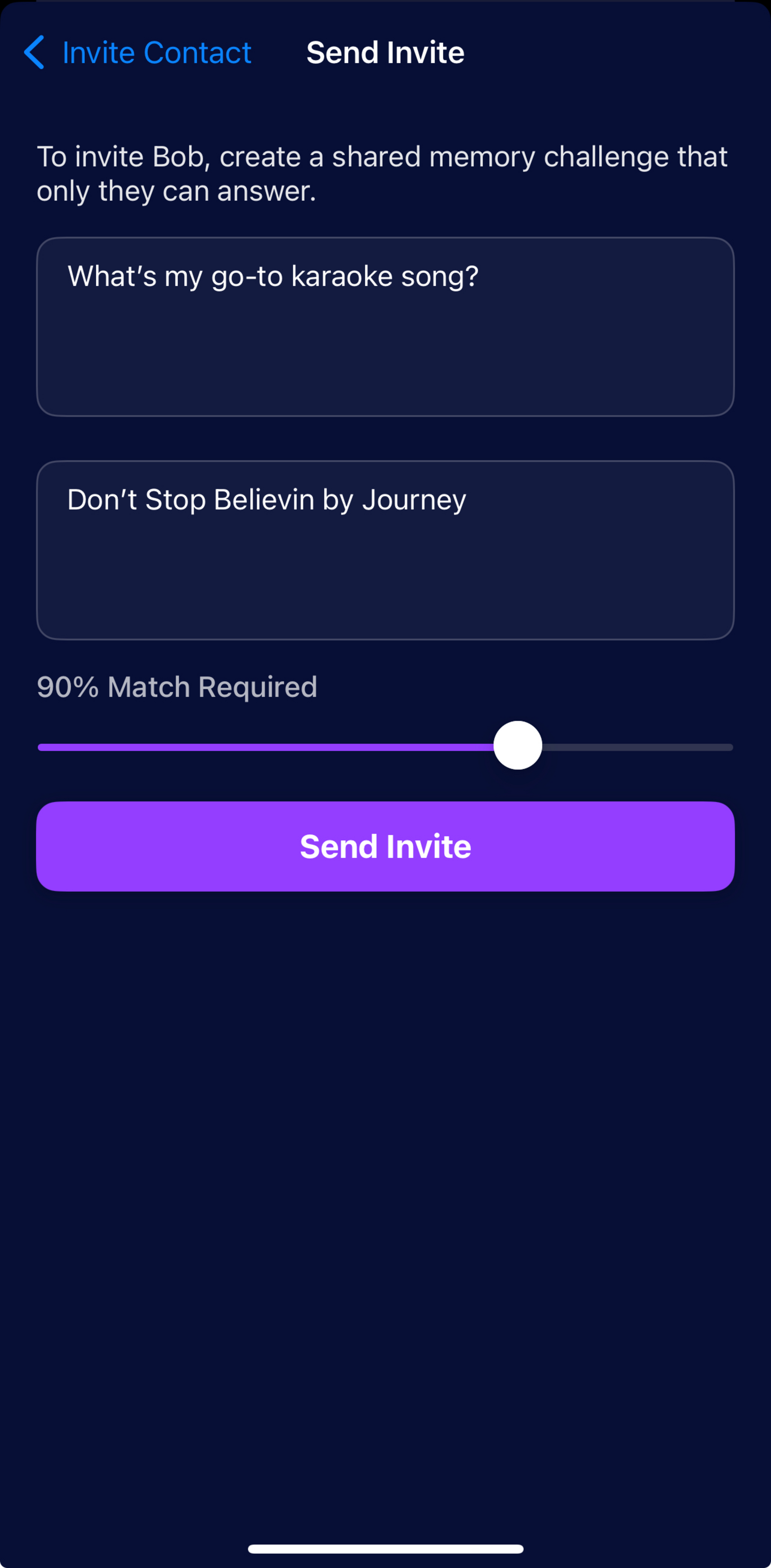
Memory Challenges
Create verification questions based on shared experiences.
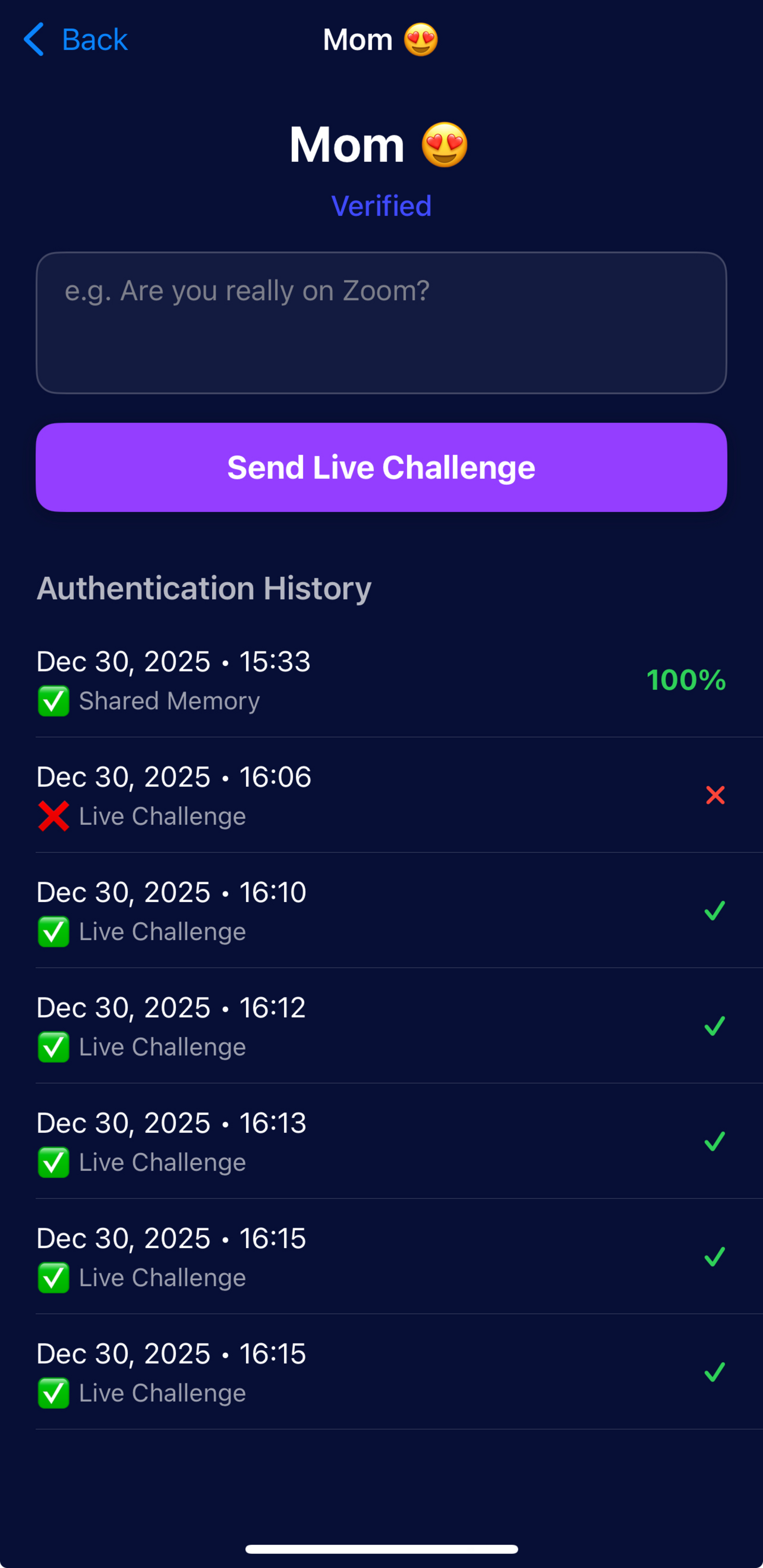
Contact History
View detailed verification history for each trusted contact.
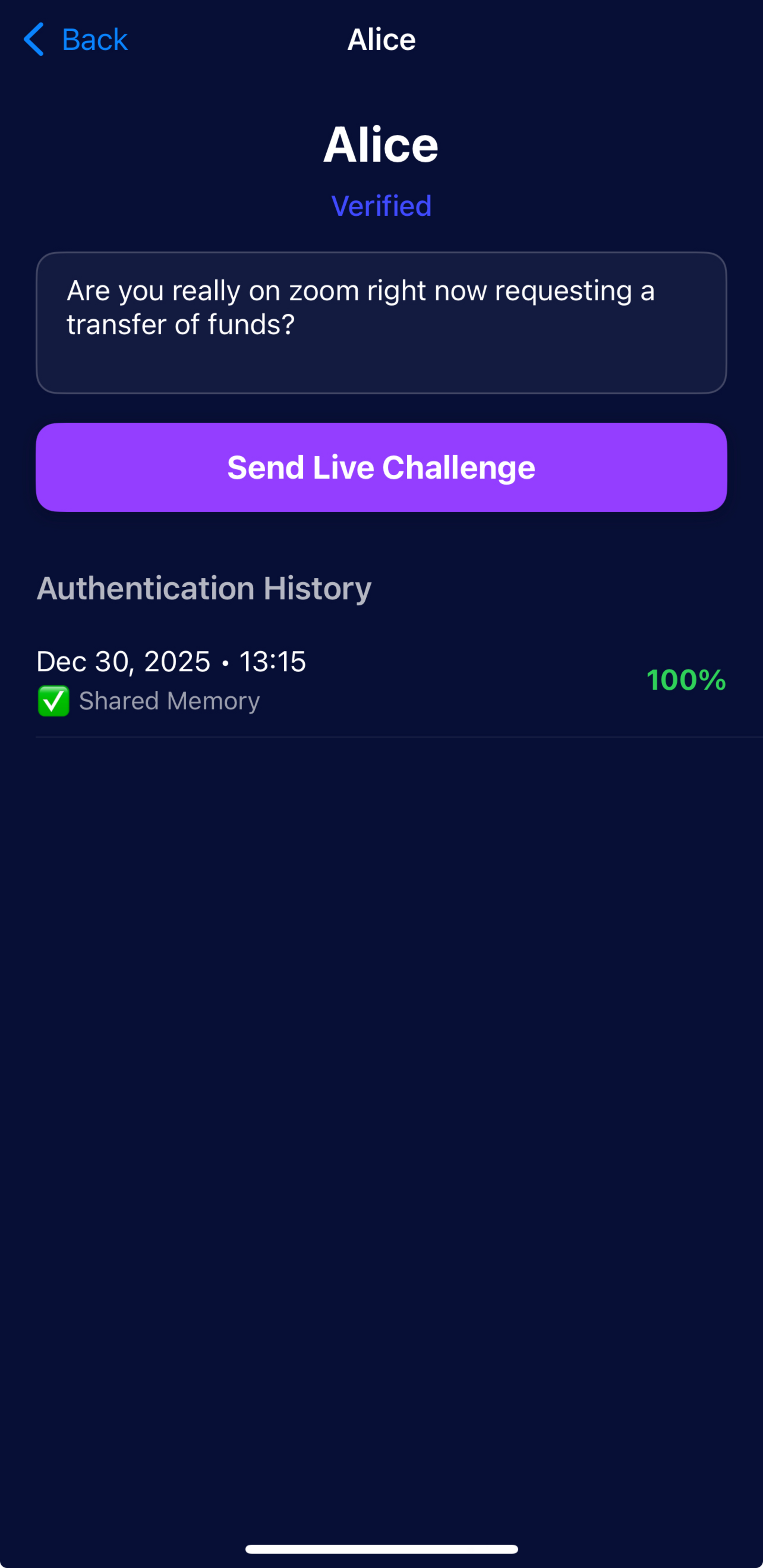
Send Live Challenges
Verify someone's identity in real-time before trusting them.
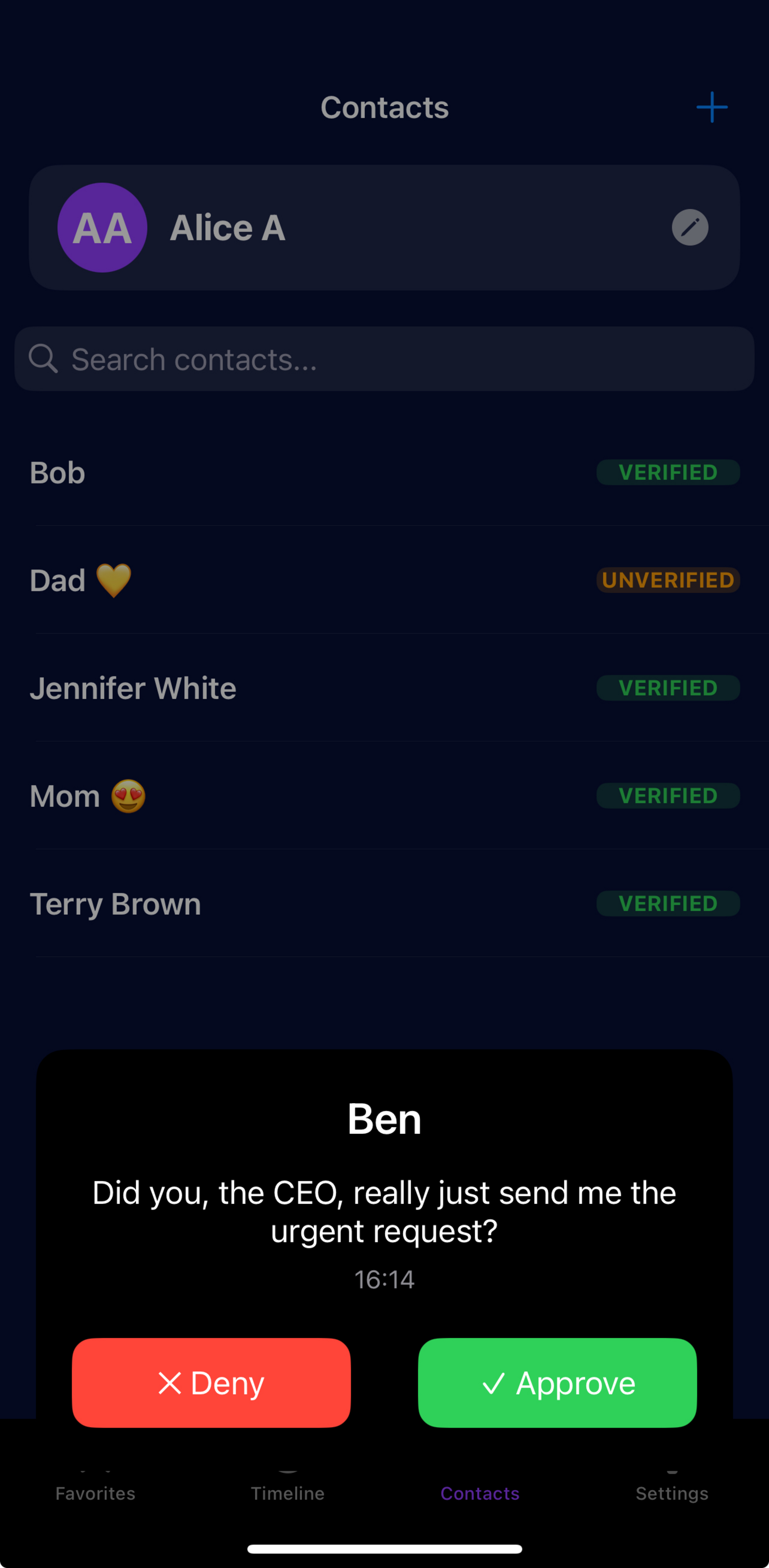
Answer Live Challenges
Prove you're real with instant yes/no verification.
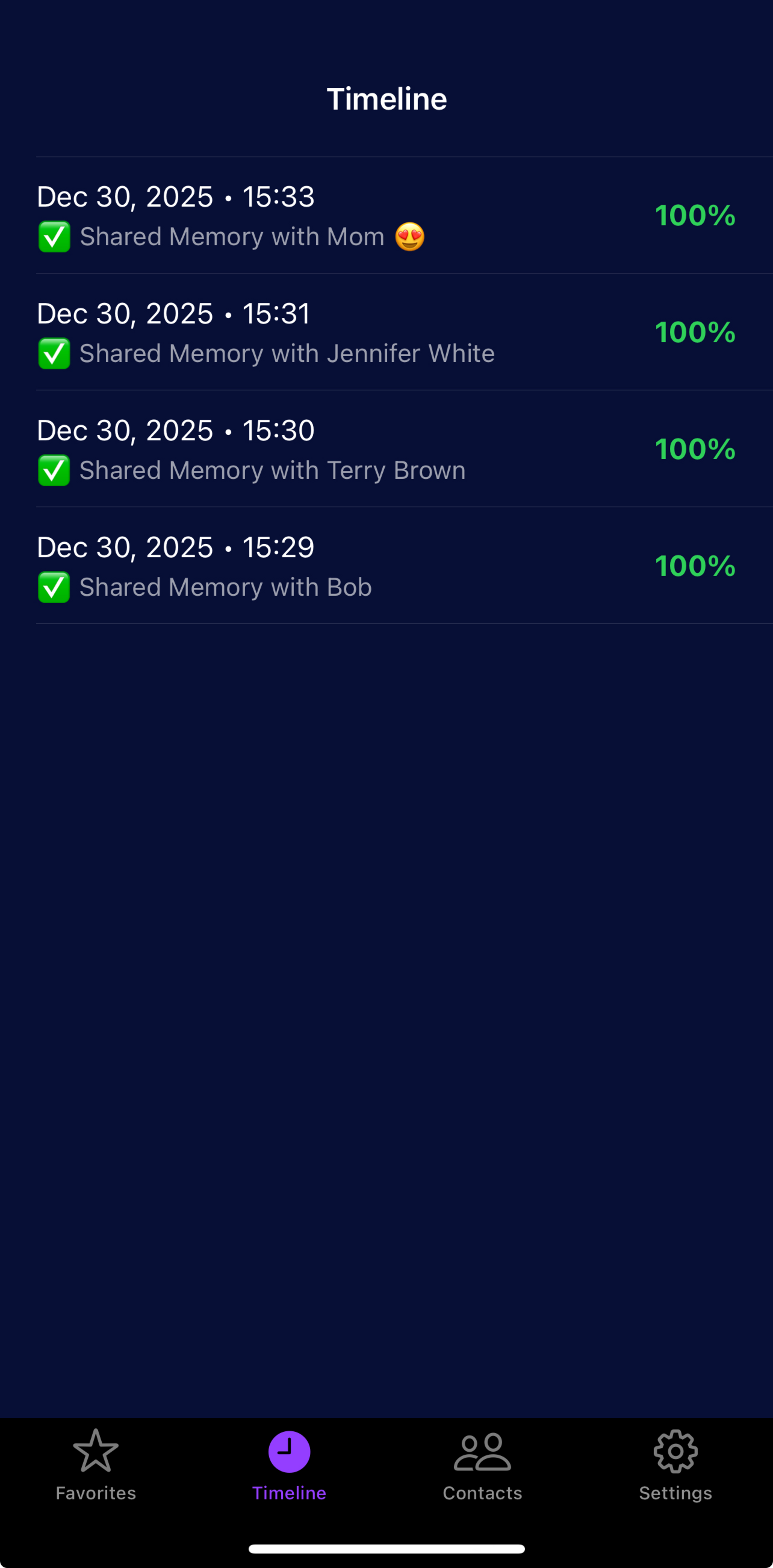
Authentication Timeline
Track all verification attempts across your network.
Who It's For
Families
Protect parents and grandparents from AI voice scams. Stop "emergency" calls from fake family members.
Executives
Prevent CEO fraud and wire transfer scams. Verify colleagues before authorizing transactions.
Journalists
Confirm sources are who they claim to be. Protect confidential communications.
Everyone Else
Anyone who wants to know who's real on the other end of a call, message, or video chat.
How It Works
Three steps to unbreakable trust
Add Trusted Contacts
Connect with people you know in real life. Each connection creates a unique cryptographic relationship.
Create Memory Challenges
Set up verification questions based on shared experiences. Only the real person knows the answers.
Verify Before Every Call
When someone contacts you, they answer a memory challenge. If it matches, you know they're real.
Powered by The Doppelgänger Protocol™
Our cryptographic protocol combines memory-based authentication with device-bound keys and biometric verification. Even if someone clones your voice and face perfectly, they can't fake your memories or access your device's secure hardware.
